In the previous article, we saw what an HSM is and why its needed in an Automotive ECU and its benefits. And we briefly touched upon EVITA and the three HSM types prescribed by HSM. In this article, lets find out in detail the definition of the three types HSM Full, HSM Medium and HSM Small, their target applications and the differences between them.
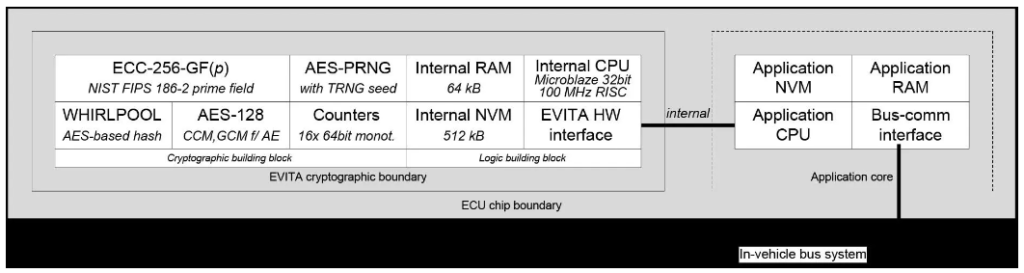
Full EVITA HSM
This HSM prioritizes safeguarding the in-vehicle domain from security vulnerabilities inherent in V2X communications. This necessitates the creation and verification of electronic signatures. To meet performance demands, a highly efficient asymmetric cryptographic engine is essential. The full HSM offers the highest level of functionality, security, and performance among all HSM variants. Additionally, it strives to provide a security lifespan of at least 20 years.
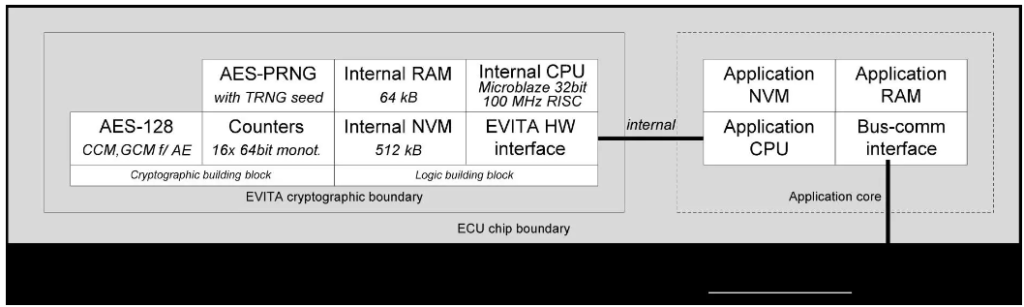
Medium EVITA HSM
This HSM prioritizes securing on-board communication. Compared to the full HSM, the medium HSM shares similar functionality, with the exception of the asymmetric cryptographic building block and a marginally slower CPU (25 MHz vs. 100 MHz). To optimize efficiency and cost, the medium HSM forgoes a hardware asymmetric cryptographic building block, but it can still perform non-time-critical asymmetric cryptographic operations in software, such as those required for establishing shared secrets. Since symmetric cryptographic algorithms are employed for virtually all internal communication protection, omitting the asymmetric crypto engine is a prudent decision that reduces hardware size and costs.
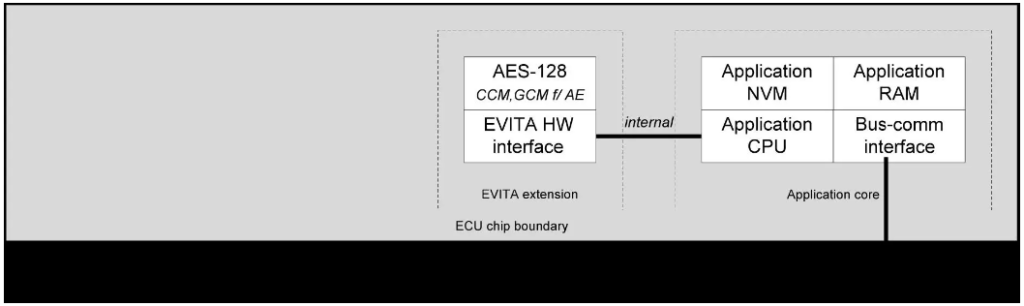
Small EVITA HSM
This HSM is specifically designed to safeguard the interactions between secured ECUs and sensors and actuators. It only requires a symmetric cryptographic engine and the corresponding functionally reduced hardware interface. This streamlined design enables the light HSM to meet the stringent cost and efficiency constraints (e.g., message size, timing, protocol limitations, or processor consumption) that are prevalent in sensor and actuator applications. Shared secrets, essential for secure communication, can be established through various methods, including pre-configuration during manufacturing, self-initialization (e.g., based on physically unclonable functions), or even by executing a key establishment protocol in software on the attached application processor.
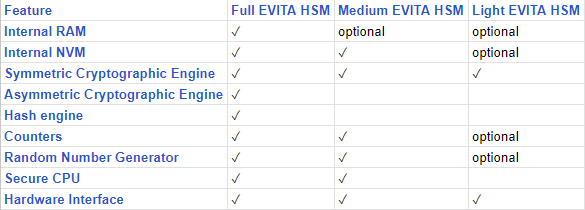
The following table summarizes the differences between the three HSM types
That’s all for now. See you!


